Introduction Mobile Touch ID

Welcome to the frontiers of secure authentication: Touch ID. In today’s digital landscape, where security is key, Touch ID stands out as a pillar of trust. This groundbreaking technology, seamlessly integrated into Apple devices, provides an easy and safe way to unlock access. Let’s take a deep look at the intricacies of Touch ID by examining its evolution, mechanics, and many advantages in this digital era.
Section 2: Evolution of Touch ID: From Inception to Integration

Touch ID has come a long way since its debut; it started as a radically new idea and quickly became ubiquitous across all Apple products. The iPhone 5S launch in 2013 marked an important shift in user authentication replacing traditional passcodes with fingerprint scanning technology.
Touch ID was initially met with skepticism but quickly gained traction among users who appreciated the speed, accuracy, and unparalleled convenience that it offered. With each new version of Apple’s devices came improvements on Touch ID thereby making it perform better while at the same time being more reliable.
This feature was expanded from Smartphones such as iPhones to other gadgets like iPads and MacBooks thus enforcing its position as one of the building blocks upon which Apple’s entire ecosystem rests. The fact that different devices could integrate Touch ID seamlessly showed how much effort apple had put into being innovative through these various things they make.
Nevertheless this development didn’t only cover hardware progressions alone. Software enhancements were also introduced by Apple for every iOS iteration to improve functionality and provide optimal performance and security for Touch ID.
The importance of Touch ID goes beyond just unlocking your device as it evolved. Now you can perform several transactions including payment authorization or accessing sensitive information with one touch because it is already your gateway.
Presently, Tech Id represents Apple’s commitment to seamless integration, intuitive design, and uncompromising security. From being a new fad to one of the most important accessories, Touch ID has become an essential item for Apple’s tech-savvy buyers and this transformation reflects not only technological advancement but also ever-changing customer preferences as part of a more virtual world.
Section 3: Understanding the Mechanics: How Touch ID Works

Touch ID combines software and hardware components that work together to produce an exceptional kind of biometric authentication. The process begins with a capacitive touch sensor that is placed on the device’s home button or power key. This sensor takes high-resolution images of the user’s finger details and applies advanced algorithms to extract distinct fingerprint attributes.
Once enrolled, Touch ID saves a mathematical representation, known as “hash,” in its secure enclave – a dedicated coprocessor for handling sensitive data. Importantly, the fingerprint data remains within your device which guarantees the highest standards of privacy and safety possible.
Whenever users try unlocking their device or authorizing some transaction, Touch ID checks if the presented fingerprint corresponds with the stored hash. In case there is a certain range for error and those two match then you’ll be granted access. It all happens in less than a second thus giving users smooth interaction while authenticating their information.
Key to Touch ID’s effectiveness is its ability to adapt to changes in the user’s fingerprints over time. Fingerprinting algorithms keep updating the stored template by addressing age-related changes or other factors that can subtly alter prints such as environmental variations so it always works well on any iPhone or iPad even after years of use.
Moreover, Touch ID employs state-of-the-art anti-spoofing technology to counter unauthorized access attempts by identifying specific living skin characteristics like pulse and temperature that distinguish real fingerprints from copies.
In summary, through advanced hardware, secure storage, and intelligent algorithms, the mechanics of Touch ID deliver prompt, correct, and reliable biometric authentication. Appreciating how Touch ID operates will allow users to understand several security mechanisms therein protecting their digital identity as well as personal information.
Section 4: The Pros of Using Touch ID Authentication
Touch ID authentication has numerous benefits that improve user experience and security in the online environment.
1. **Convenience**: Gone are the days when unlocking devices or authorizing transactions was a hassle with passcodes or patterns; using a fingerprint on a touch ID is both seamless and effort-free. This attribute is especially useful when situations require accessing quickly such as payment transactions or urgent information.
2. **Enhanced Security**: Inherent to its design, biometric authentication offers a higher level of security than other methods such as passwords or PINs. By reducing the risk of unauthorized entry through very hard-to-forge fingerprint patterns, touch id leverages on uniqueness of each pattern. It also enhances protection against remote hacking since it does not send your fingerprint data across the internet but keeps it locally within your phone only.
3. **User Experience**: Besides safety, Touch ID makes everything easier in terms of authentications for different applications and services used. Touch ID offers app login details, and app authorization among others which all have echoes indicating consistency thereby lessening friction and resulting in increased ease of use.
4. **Accessibility**: Accessibility barriers are lowered through technology like touch id which is inclusive for people with various forms of impairments including those related to traditional means of identification used during authentication processes. To this end, touch id’s simplicity combined with reliability ensures that everybody can use it regardless of age or disability hence improving inclusivity in digital platforms worldwide.
5. **Integration with Ecosystem**: Touch ID is seamlessly integrated into various Apple devices such as iPhones, iPads, and MacBooks for those who are part of the Apple ecosystem. By ensuring consistent authentication standards across all devices this unified user experience improves not only convenience but also overall security from an ecosystem perspective.
6. **Efficiency**: Notably, touch id authentication is fast and efficient thereby cutting down on the amount of time and effort expended during authentication tasks. So when it comes to unlocking a device, checking out, or any other sensitive information, touch id streamlines the process thus enabling users to do what they need to without much disruption.
In summary, Touch ID is more than just convenience; it offers improved security, better usability, accessibility for everyone, integration into ecosystems as well as efficiency. Thus, using biometric verification methods like touch ID changes how people interact with their digital gadgets resulting in greater safety and user-friendliness towards future developments.
Section 5: Security Measures and Biometric Accuracy
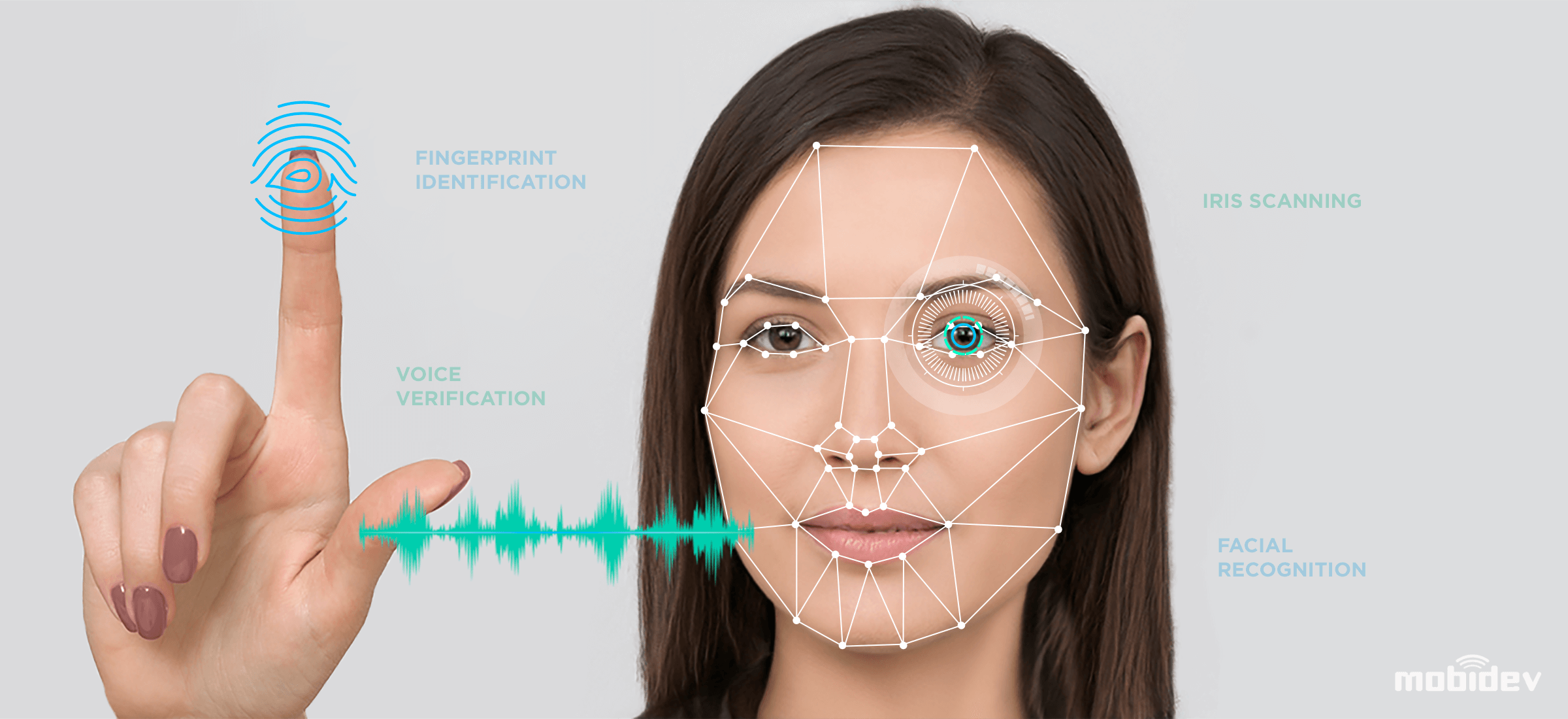
The reliability of Touch ID as a security mechanism lies in its solid construction and accurate biometrics that guarantee trustworthy identification while maintaining the privacy of customers.
1. **Biometric Accuracy**: Touch ID utilizes advanced capacitive touch sensor technology to capture high-resolution pictures of a user’s fingerprint. These images are then passed through sophisticated algorithms that extract peculiar features like ridge patterns and minutiae points. With the aid of these, Touch ID has achieved a very high level of biometric accuracy lowering false acceptance rates (FAR) and false rejection rates(FRR).
2. **Secure Enclave**: The secure enclave is a specialized coprocessor located within Apple devices that acts as the security core of Touch ID. This enclave keeps sensitive user information like fingerprint templates in an encrypted environment that is separate from other parts of the device. By keeping the fingerprints confined to the secure enclave itself, unauthorized access or tampering with the contents becomes less possible.
3. **End-to-End Encryption**: To ensure authenticity, integrity, and confidentiality of fingerprint data, it makes use of the end-to-end encryption mechanism discussed below: When someone registers his/her fingerprint on touch ID, it generates a mathematical summary known as a hash. This hash is encrypted using some specific keys that belong to that particular device alone; hence forming an extra layer of security for such hash-key combinations which will further be stored inside a secure enclave where no one can have direct access to them. So, during the authentication process when a person presents his fingerprint it will be verified by comparing this new figure produced against what had been said above which means real fingerprints data remains encrypted and thus inaccessible except for authorized persons only.
4. **Anti-Spoofing Measures**: To forestall fraudulent entry via spurious or counterfeit fingerprints Touch ID incorporates elaborate anti-spoofing measures into its design. Some of these measures include identifying attributes unique to living skin such as pulse and temperature to differentiate between genuine finger surfaces and those made artificially or by machines with metal films or even gels. The Capacitive touch sensor also manages fine distinctions between the electrical conductivities to differentiate between real and artificial fingerprints.
5. **Continuous Learning**: Touch ID is built with a machine-learning algorithm that can adapt to changes in the fingerprint over time. As users interact with their devices, the stored fingerprint data gets updated by Touch ID for optimum performance and accuracy. This feature allows Touch ID to accurately recognize even slightly changed fingerprints caused by factors such as age or environmental conditions.
To sum up, these security measures combined with biometric accuracy make Touch ID a strong and reliable authentication system. By using advanced technology, secure encryption, and continuous learning algorithms, Touch ID sets the industry standard for biometric authentication providing secure access across all Apple devices.
Section 6: Touch ID Across Apple Devices: Compatibility and Integration
The ease with which Touch ID can be integrated across a range of Apple devices is proof enough of its versatility and usefulness in contemporary digital ecosystems.
1. **iPhone**: The iPhone 5S was the first device to use Touch ID, which now serves as a standard feature on all iPhones from the compact iPhone SE to the flagship iPhone 13 Pro Max for unlocking, payment purposes, or accessing personal data.
2. **iPad**: In addition, iPads have been enhanced by this integration of Touch ID thereby improving their performativity and security. Consequently, users can unlock their devices, secure personal information, and verify app purchases like never before on any iPad such as entry-level models and powerful iPad Pro.
3. **MacBooks**: Besides mobile gadgets, MacBook line-ups now come with Touch ID which has significantly transformed how users connect with their laptops. With Touch ID-enabled MacBooks, users can unlock them without typing in any password at all thus allowing system changes authorization and safe payments using Apple Pay among others.
4. **Integration with macOS**: Moreover, it goes beyond unlocking devices and authorizing payments; hence smoothly fitting into macOS to increase overall user experience quality. For example, when one uses a MacBook that supports touch IDs else he or she has fingerprint recognition capabilities in order to log in securely access encrypted file as well as authorize admin tasks by simply putting finger on keyboard thereby simplifying workflow intensifying safeguarding functions.
5. **Third-Party App Support**: Consequently, third-party applications developers who integrate biometric authentication through touchID APIs make it possible for such apps as password managers, banking applications or document vaults to have sensitive data protected using familiar touchIDs rather than alternative methods of authentications yet being used today by diversified firms who rely on this option provided by various other companies.
6. **Future Prospects**: It appears that there are brighter prospects ahead for the future of Touch ID as Apple continues to invent and refine its product line. For instance, rumors already have it that under-display touch IDs are in development along with advancements in biometrics technologies such as Touch ID to guarantee security and ease of use according to Apple’s commitment on the matter regardless of its diversified devices.
In a nutshell, compatibility and integration through Touch ID across Apple’s ecosystem change how users relate to their gadgets. This is achieved by ensuring that iPhones, iPads, MacBooks, and macOS ensure consistency and ease during authentication processes thus enhancing security, facilitating operations at work place as well as promoting user experience in this digital era.
Section 7: Enhancements and Future Prospects of Touch ID
Touch ID has come a long way through continuous enhancements towards an exciting future.
1. **Improvements in Accuracy and Speed**: In terms of accuracy and speed, Touch ID technology has undergone significant improvements over time. By making iterative hardware and software updates, Apple has been able to fine-tune touchID sensors along side algorithms which have helped improve the rate of false rejections while boosting the overall identification rate speedily increasing authentication levels that go a long way in improving security while offering a more seamless user experience.
2. **Expansion of Biometric Capabilities**: Although initially focused on fingerprint recognition capabilities only, future versions might expand the range of modalities covered by touchIDs. There are unconfirmed murmurings indicating that Apple could insert facial recognition or other forms of biometrics into these beneath-display touch IDs or any other potential fingerprint authentication alternatives. These multiple factors might further increase convenience among users while maintaining secure access points within their systems thereby contradicting most assumptions about security matters related to these innovations regarding apple products’ technology orientations the company made earlier leading to a greater safety net for customers than ever before.
3. **Incorporation with New Technologies**: Touch ID is expected to merge into new trends like augmented reality (AR) and wearable technology as technology advances. Imagine a scenario where AR-based applications could use Touch ID for user authentication, or smartwatches and AR goggles are unlocked by it. By using Touch ID’s reliability in terms of security and its friendly user interface, Apple will be able to move closer to the unknown territories of digital interaction.
4. **Improvements in Privacy and Security**: In future editions, Touch ID may also include other privacy features and enhancements for security that are responses to concerns regarding data privacy and security. This may entail improvements in encryption protocols, more robust anti-spoofing measures, or greater transparency on how biometric information is used. If Apple places user’s privacy and safety first concerning this Touch ID technology, users will keep trusting it.
5. **Integration With Apple Services**: Since digital services have become important aspects of everyone’s daily lives, Touch ID will primarily be used as a means of securing access to the entire suite of Apple services. The primary usage areas for the fingerprint sensor would include authenticating transactions via Apple Pay; gaining entry into iCloud; unlocking different productivity apps within the Apple product line among others—for all these purposes, one can rely on an uninterrupted service supplied by Apple Touch ID.
6. **Innovation/ Choice**/**Personal Customization**/**Unique Features**: What if later versions of touch-id were designed in such a way that they come with customization options allowing users to choose what their authentication experience looks like? Some of the functionalities that can be customized include sensitivity settings based on personal preferences or alternate ways through which someone can authenticate themselves besides their fingerprints or come up with personalized biometric profiles that change according to characteristics that differ from one individual user to another over time.
In conclusion, there are great prospects ahead as far as improvement and exciting possibilities are concerned for touch-ID. This future will be built on new technologies, privacy and security concerns as well as user customization in terms of the technology involved.
Section 8: **Implementing Touch ID into Everyday Life Scenarios**
Touch ID has extended its usage to other practical applications beyond device unlocking, which enhances convenience and security for users in different everyday scenarios.
1. **Device Unlocking**: Primarily, The main purpose of implementing Touch ID is to make it easier to unlock devices like iPhones, iPads, or even MacBooks. Touch ID replaces the need for long pass codes with a simple fingerprint scan hence making it quicker and less daunting to access digital gadgets.
2. **App Authentication**: With Touch ID users can use this authentication system through their apps by just scanning their fingerprints and gaining access to all kinds of sensitive data or perform authorized actions without having to remember any passwords at all. Banking apps’ login verification; password managers’ login verification; authorization of in-app purchases – these are just a few examples that demonstrate how seamless and secure this method is.
3. **Apple Pay**: In Apple’s mobile payment system, Apple Pay, touch-ID plays a key role in securing the transactions made through it. It guarantees an extra layer of safety against financial transaction crimes by digitizing payments using biometric identification techniques instead of traditional finger-savvy transactions.
4. **Password Management**: While assisting with managing and accessing passwords easily password managers also add more security layers through toucIDid integration. By integrating Touch ID, users can securely unlock their password vaults and autofill login credentials for websites and apps without the worry of forgetting complex passwords every time you have a login screen displaying up before you know it…. **Document Security**: Touch ID beefs up documentation security by providing a safe way to access confidential files and documents stored on Apple devices. Using Touch ID-enabled encryption, users can secure their private stuff such as; personal papers, financial records and so much more guaranteeing that this information shall be accessed only by authorized individuals.
6. **Data Protection**: Privacy of data is further enhanced through Touch ID in addition to individual applications by securing device settings, system preferences and personal information stored on Apple devices. By using fingerprint authentication to verify sensitive actions like adjusting the device settings or opening user profiles, it ensures data protection from unauthorized accesses hence upholding privacy.
7. **Multi-User Support**: With Touch ID, multiple users can log into their profiles and accounts in shared devices thus enhancing privacy with regards to their data. With the facility of touch identification, it becomes easy for account holders to switch between different accounts without compromising security as well as the integrity of data.
In summary, beyond just unlocking your phone or app there are many other areas where touch ID is applicable including those that require security convenience and user experience in the middle of them all leveraging the intuitive method of authentication that is used by touch id provides a sense of confidence when navigating digital platforms given that users know that their data is protected and easily retrievable at any point in time.
Section 9: Addressing Concerns: Privacy and Data Protection with Touch ID
Despite numerous advantages of security and ease of use, some concerns about privacy and safety must be settled for users’ reliance on these technologies.
1. **Local Storage of Fingerprint Data**: Fingerprint data storage has been one major issue associated with biometrics authentication like touch ID among others. In addressing this concern, apple clarifies that finger print is stored on a device’s secure enclave rather than being stored in the cloud or servers possessed by apple itself hence embracing a local storage mechanism for any fingerprints entered into the device. This ensures that fingerprint data is encrypted and therefore cannot be accessed by unauthorized persons thus minimizing the possibility of a data breach or improper access.
2. **Encryption and Security Measures**: Touch ID provides robust encryption and security measures to ensure the safekeeping of fingerprint information and preserve user privacy. The fingerprint information is encrypted with a key specific to each device, and it is securely stored in a secure enclave which makes it inaccessible to any malicious actor who may want to have unauthorized access to it. Moreover, Touch ID has incorporated anti-spoofing measures that prevent fake fingerprints from being used for unauthorized purposes hence boosting data security in this case.
3. **Transparency and User Control**: Apple takes transparency and user control seriously in handling finger print data. There are options for users to activate or deactivate touch ID on their devices when it comes to unlocking their phones; logging into different apps or completing a transaction using apple pay among others. Additionally, Apple has gone further to explain how touch ID works as well as the measures used in safeguarding fingerprint data thereby giving customers more choices about their privacy settings.
4. **Legal and Regulatory Compliance**: Apple’s compliance with privacy regulations has made sure that its touch id product meets all legal requirements toward protection of biometric data. This includes mechanisms such as seeking permission from users before collecting such information through the necessary steps like retaining it for a given period, or destroying it when required by legal frameworks guiding biometric authentication procedures. By meeting all legal obligations and adhering strictly to regulatory requirements, Apple showcases its commitment to customer confidentiality coupled with the security of personal records on its products where TouchID is found
5. **Regular Security Updates**: Apple frequently updates its software and releases security fixes to improve the vulnerability of biometric authentication features including Touch ID. This does not only seek to perfect the performance and reliability of Touch ID, but also tackle emerging threats, and vulnerabilities, and guarantee that users’ fingerprint data remains safe from evolving security vulnerabilities.
In conclusion, although privacy and data protection concerns are genuine, Apple has done a lot to address them and make certain that Touch ID is still a secure and reliable authentication method. Apple’s commitment to safeguarding user privacy and data security in the digital age is further underscored by the fact that it has been giving priority to local storage, encryption, transparency, legal compliance as well as continuous security updates.
Conclusion
Touch ID – with its wonderful intuitive biometric technology – become the epitome of seamless security which has revolutionized digital authentication processes. The advancement of this feature portrays Apple’s yearning for better user experiences while setting benchmarks for confidentiality. Consequently, it has promised even more integration and improved safety measures for the future significance of Touch ID in shaping the digital world. Therefore as a signpost for trustworthiness within secure consumer-oriented identification schemes; Touch ID will continue leading the way

